Fraud Schemes Exposed
Explore the latest scams and fraud tactics uncovered by Sift’s Trust and Safety Architects.
The Global Fraud Economy
Fraudsters have evolved from siloed attacks to a full-blown Fraud Economy—a sophisticated and interconnected network of cybercriminals looking to exploit online businesses.
ATO-as-a-service
Fraudsters Use Automation to Accelerate Attacks
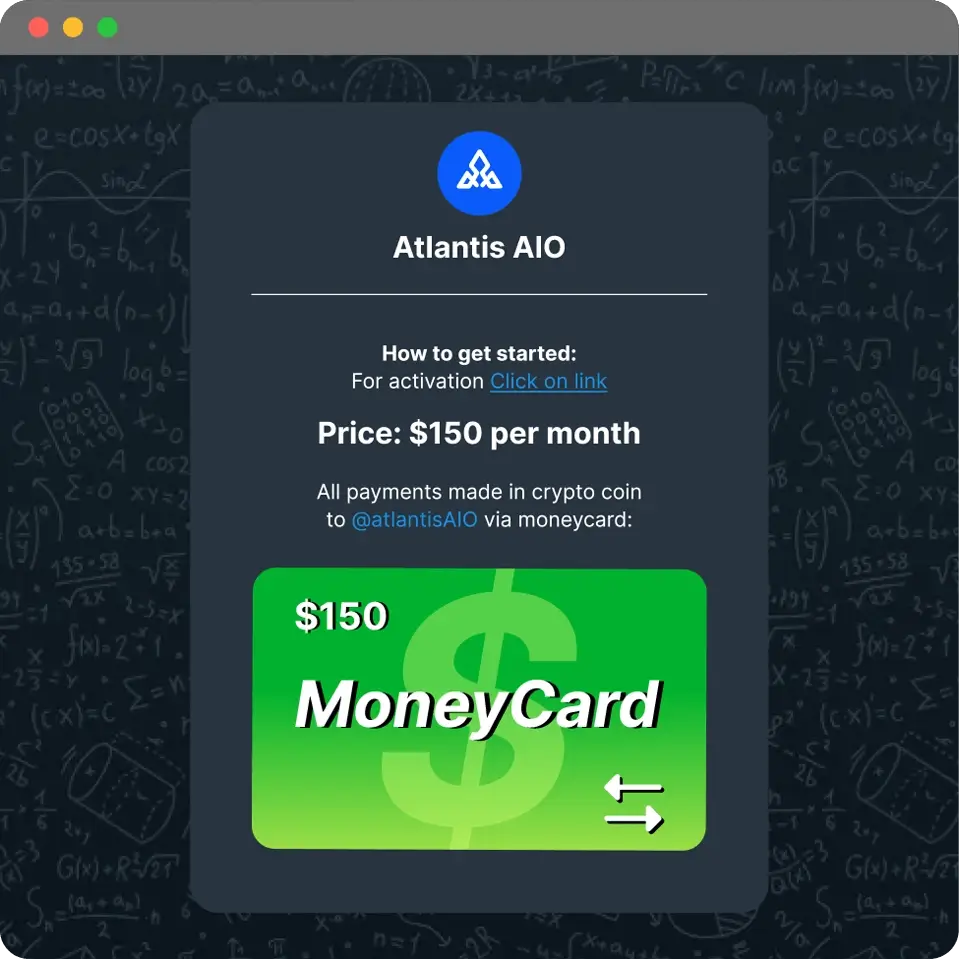
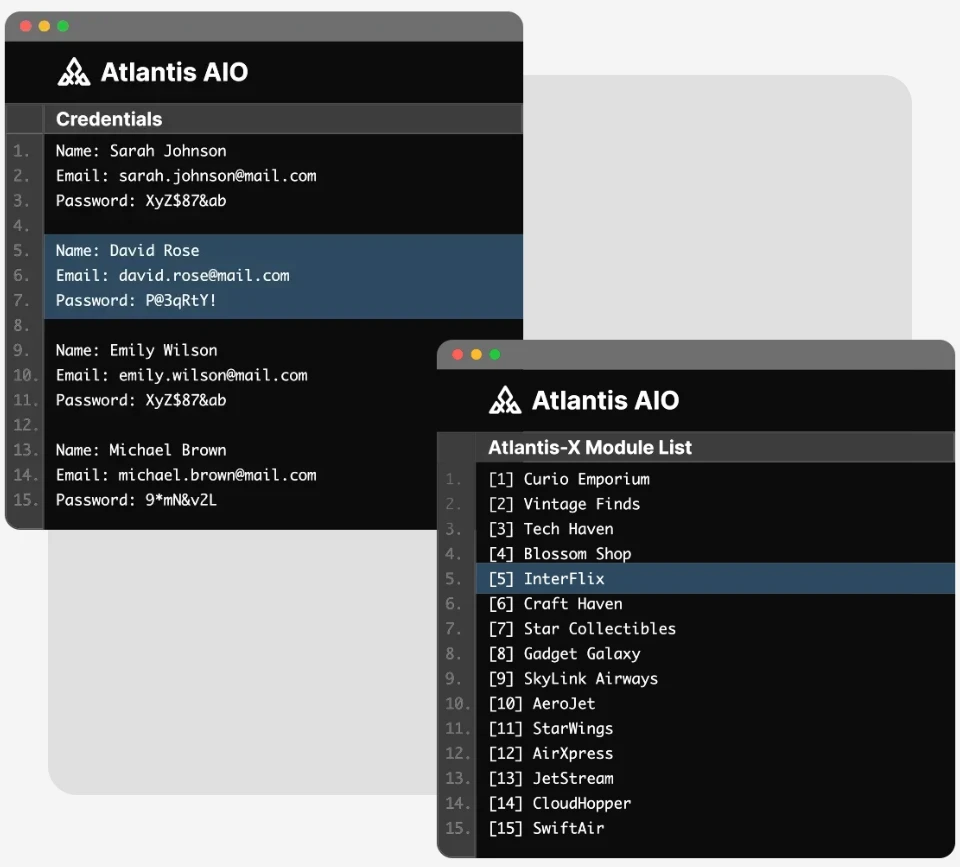
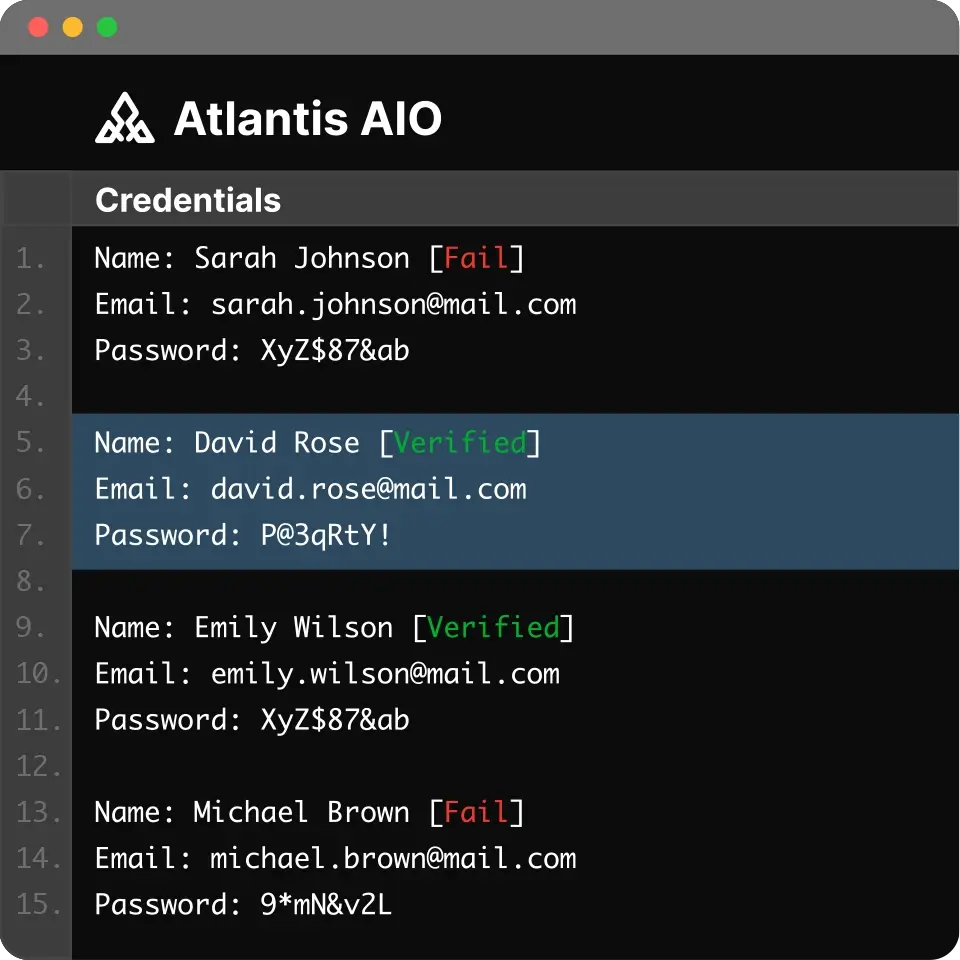
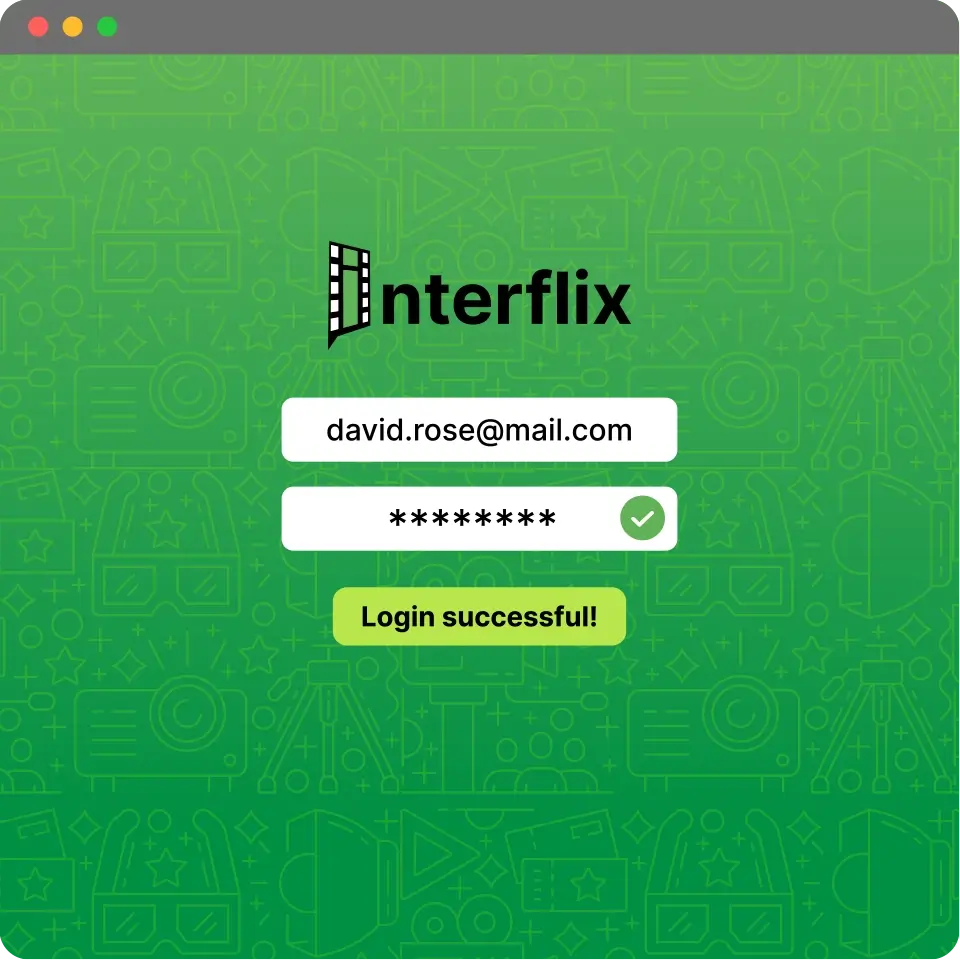
Atlantis AIO (also known as Atlantis-X) is a fraud-as-a-service credential stuffing tool, accessible via a simple link for $150 per month.
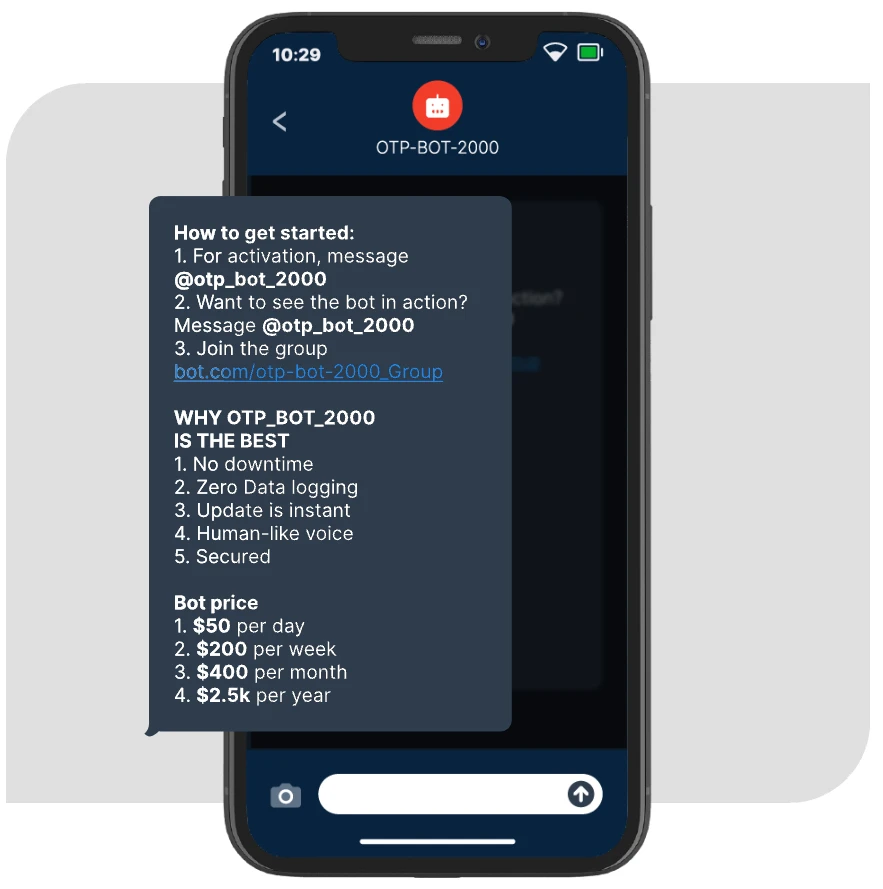
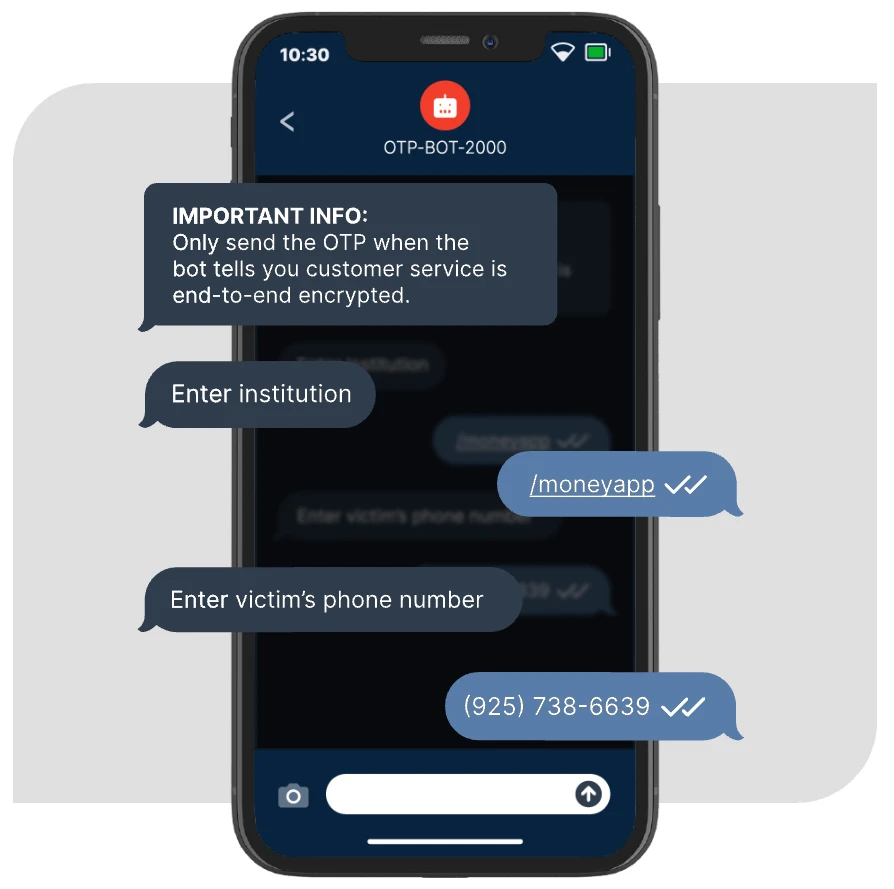
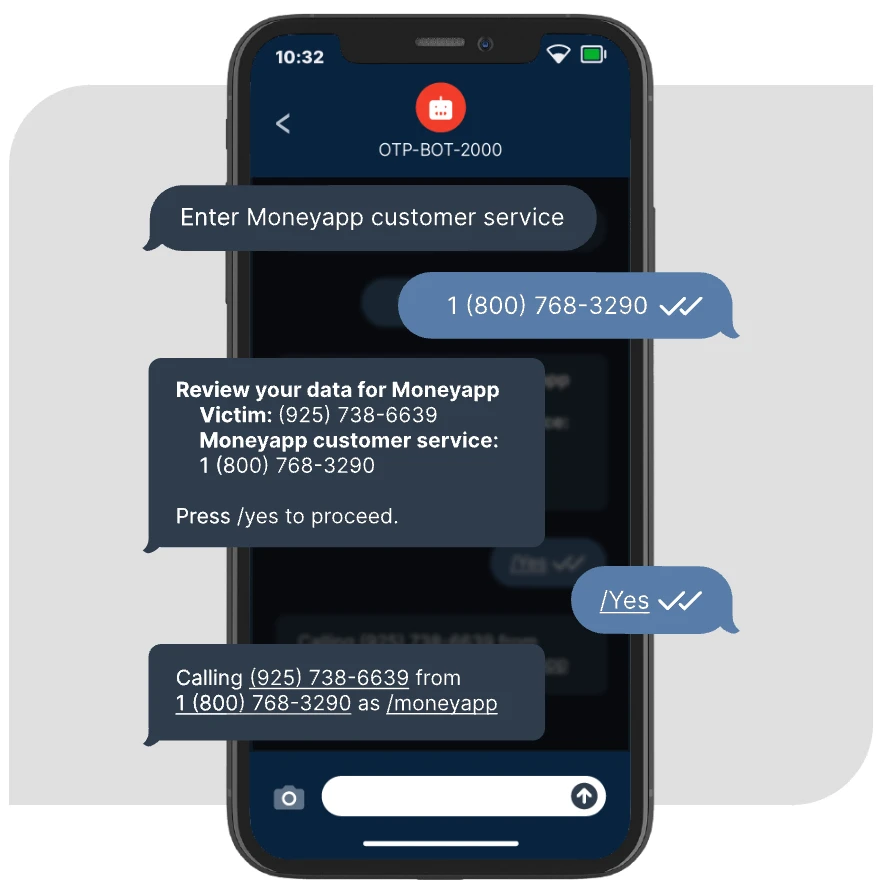
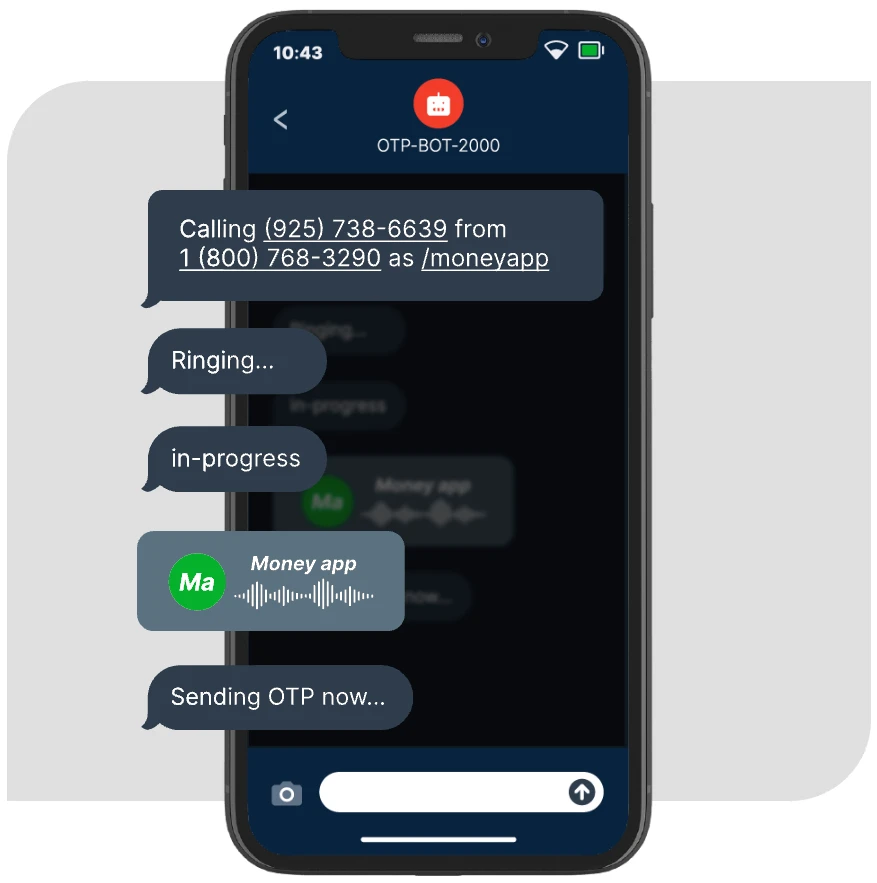
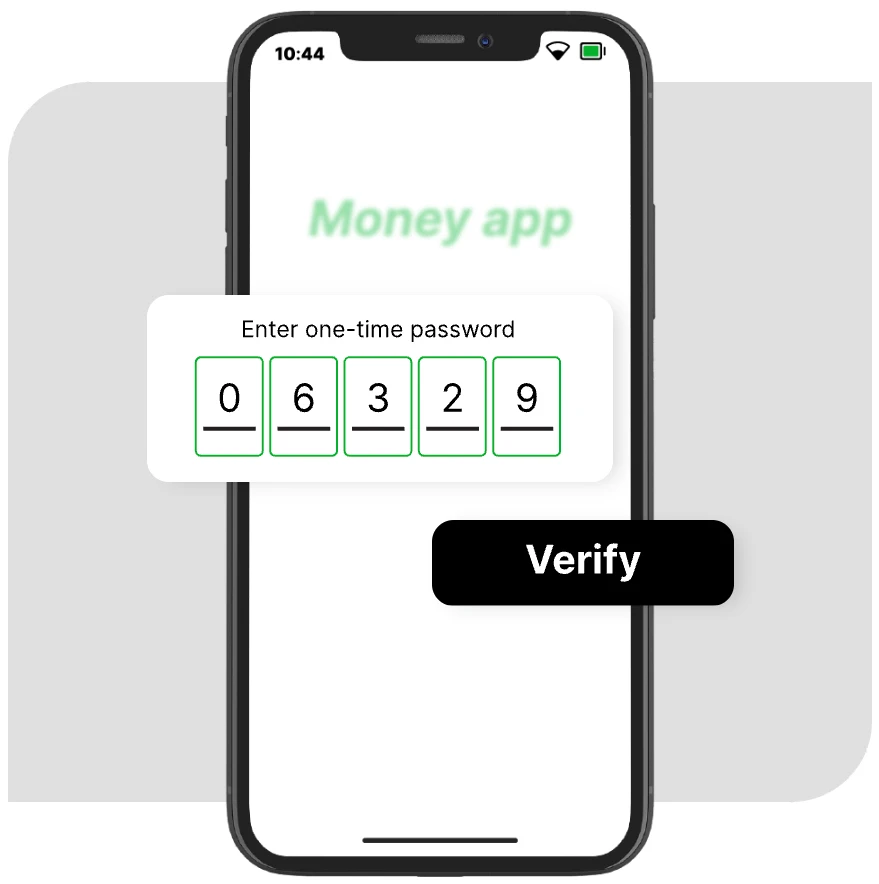
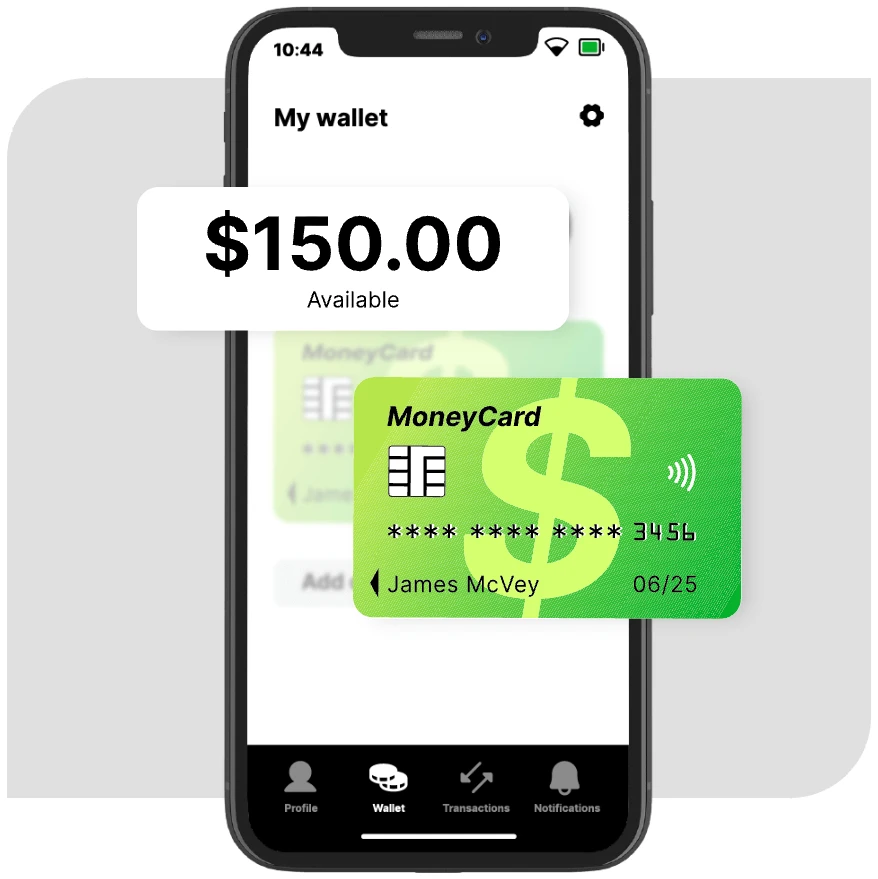
Bots-as-a-service
Mechanics of an Automated Scam
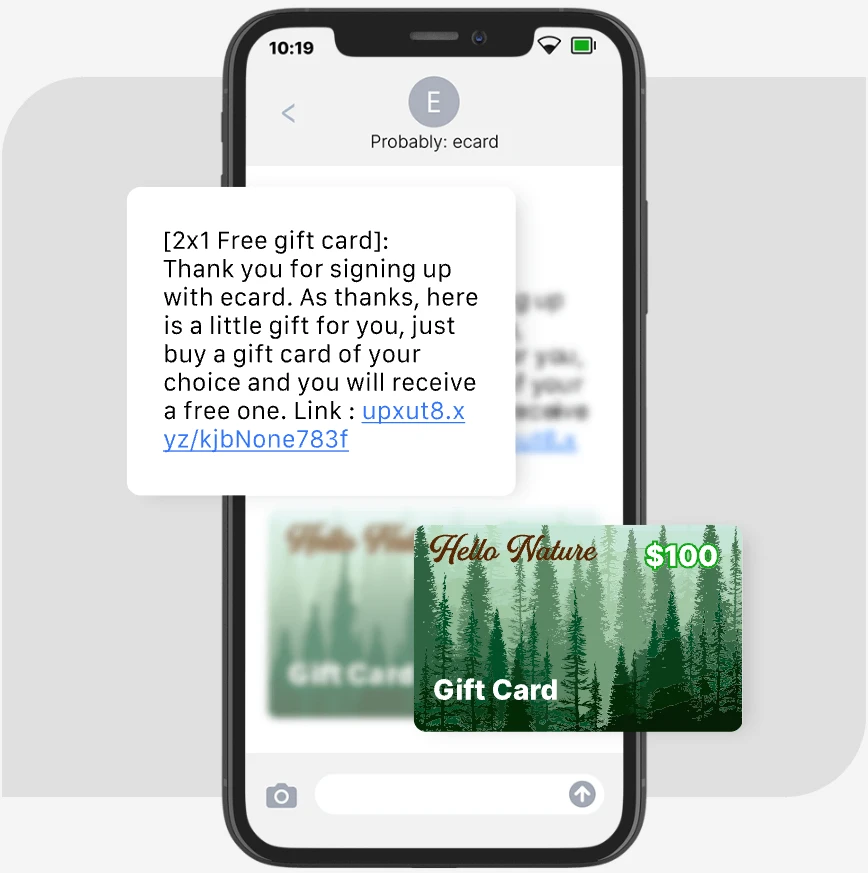
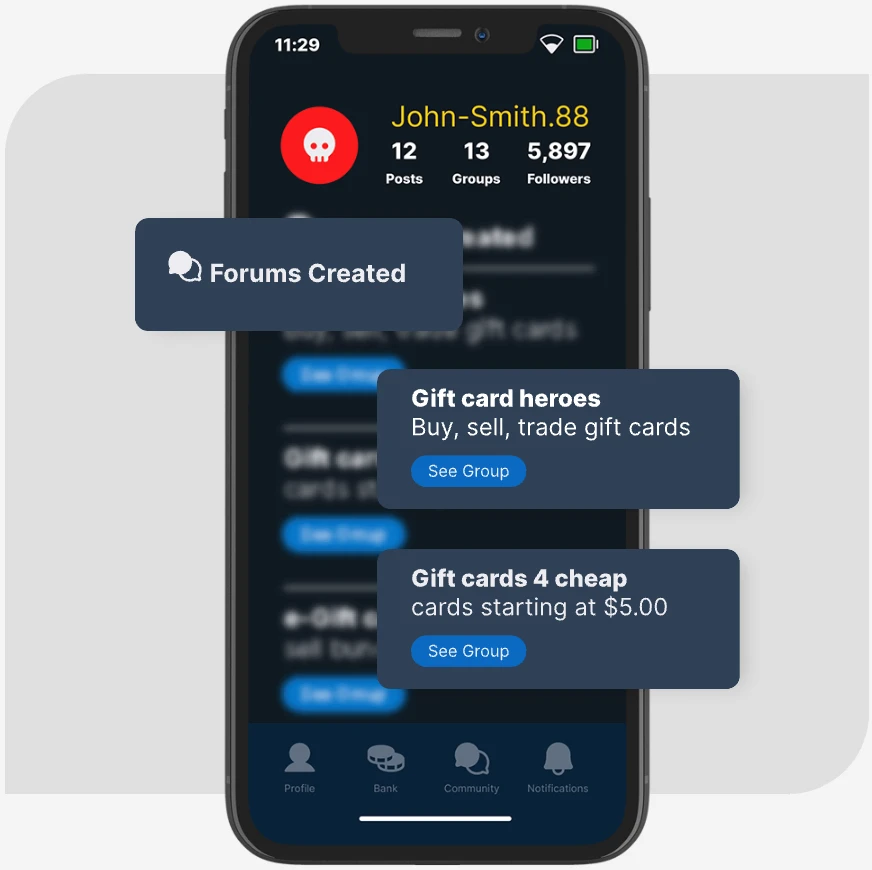
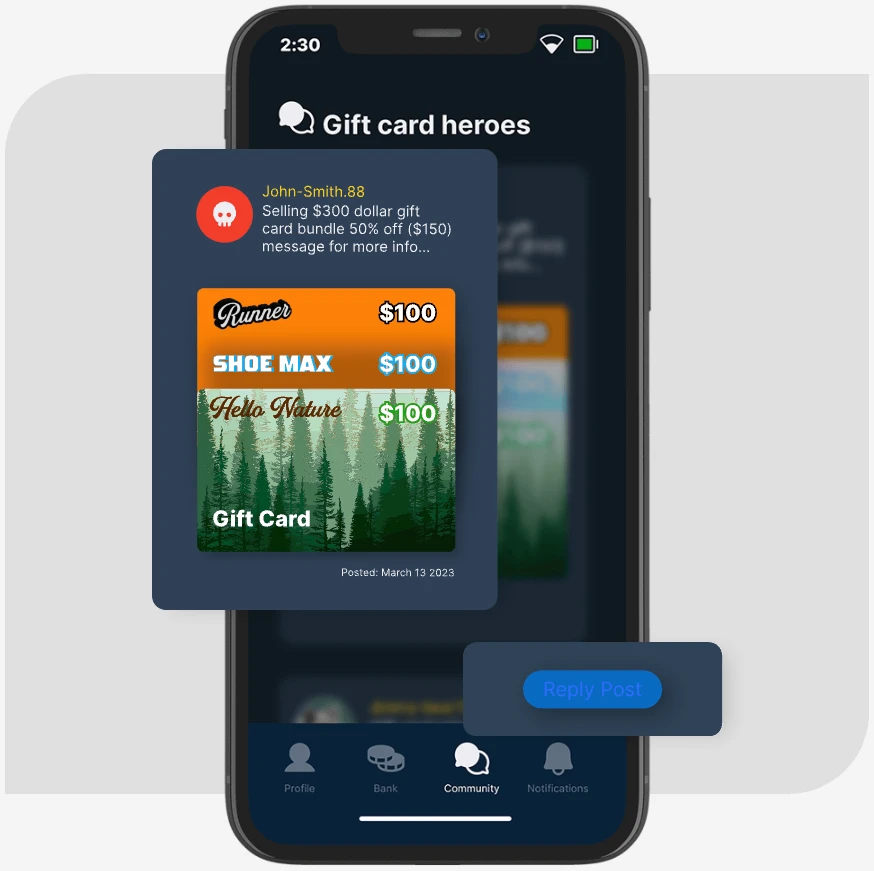
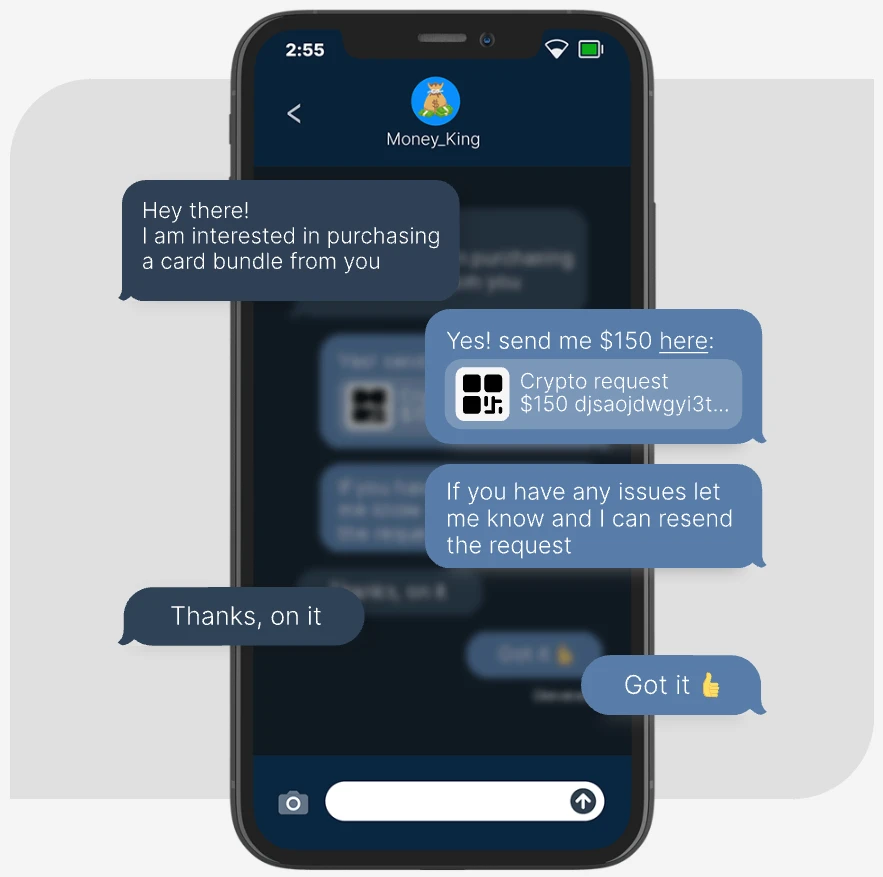
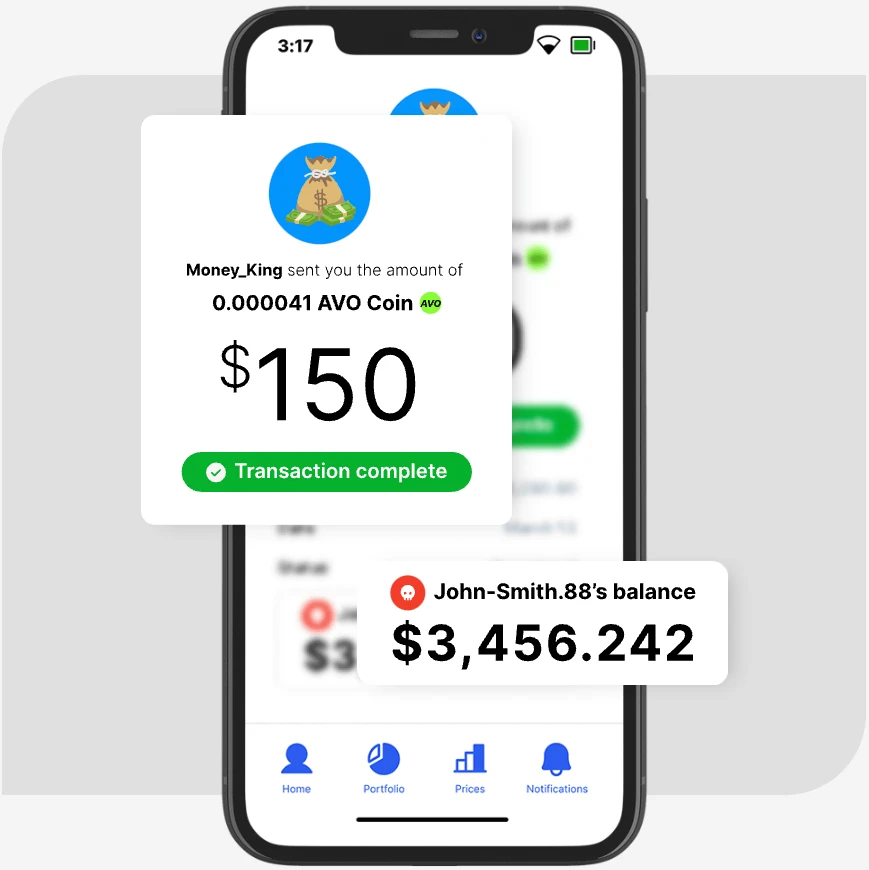
Fraud-as-a-service
Mechanics of a Criminal Business Model
Fraud attacks in one industry impact every industry.
The Fraud Economy is an interconnected web of fraud and abuse vectors that influence and impact one another. Explore data insights from the Sift global network of more than one trillion eventsper year, representing over 34,000 sites and apps across multiple industries, and learn how cybercriminals leverage the Fraud Economy to target businesses and consumers around the globe.
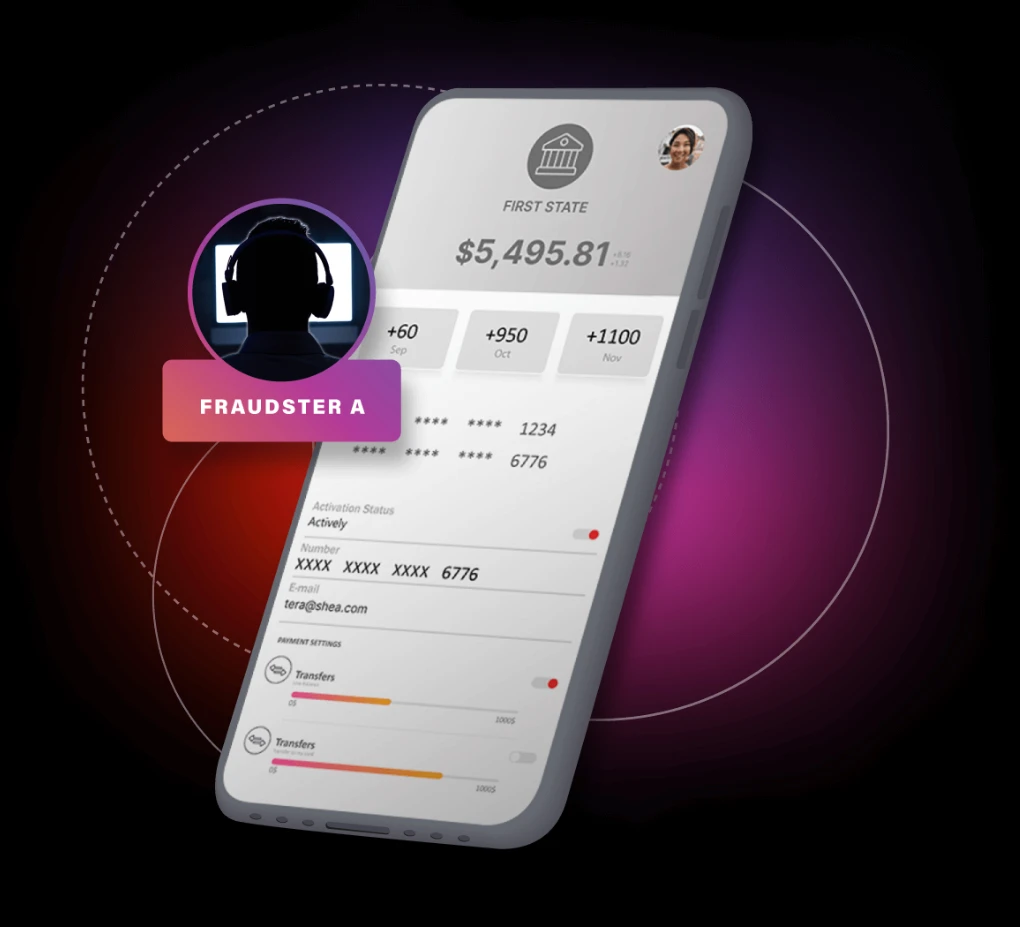
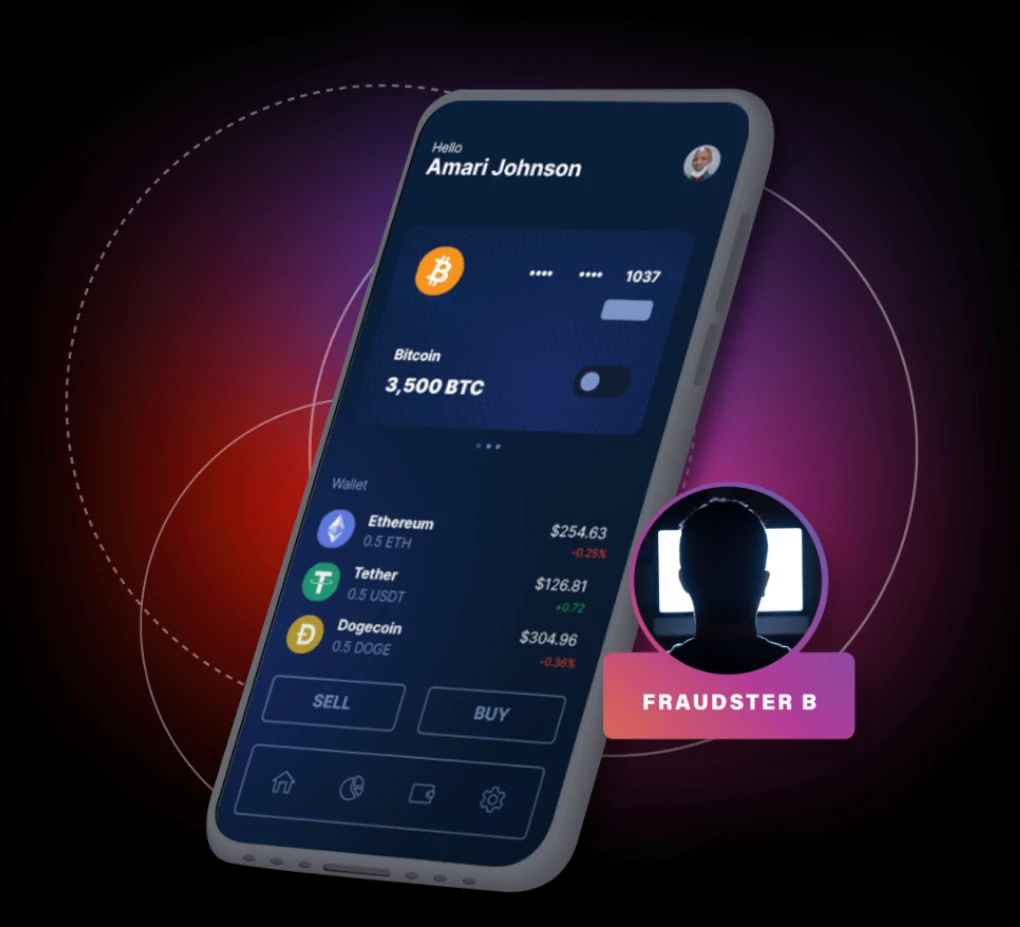
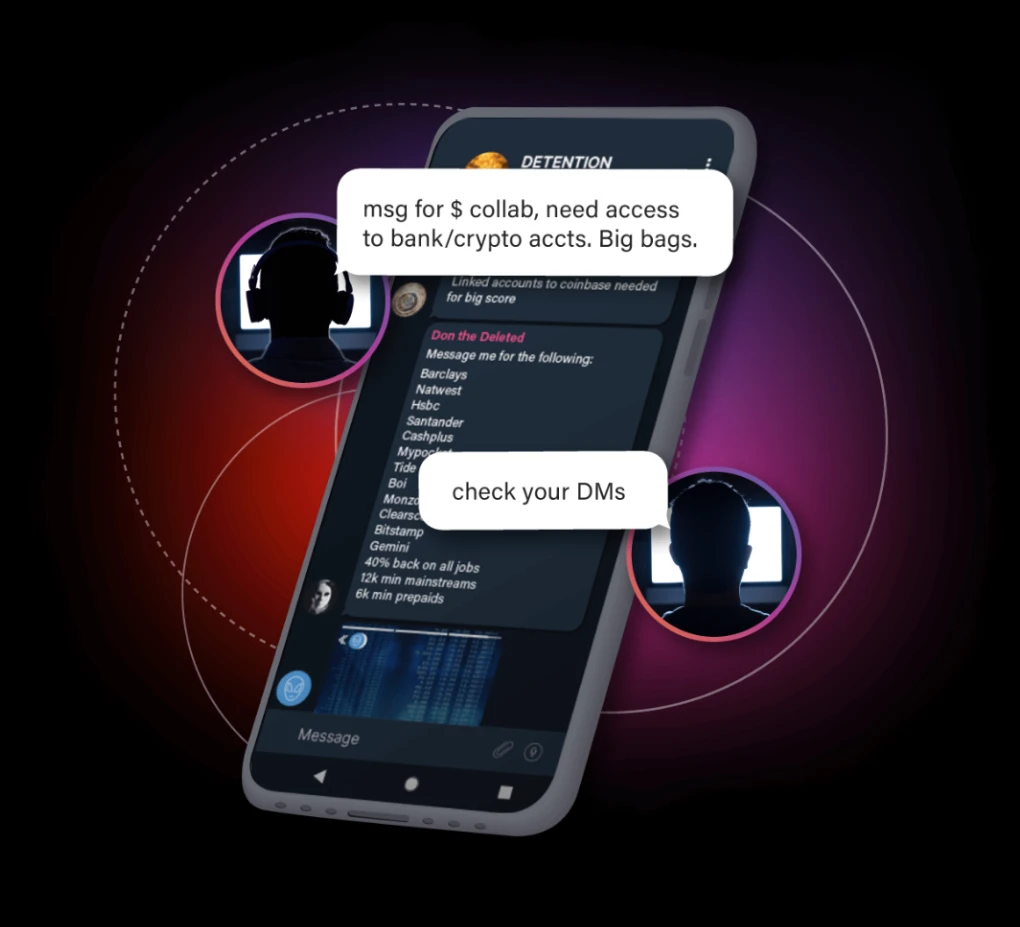
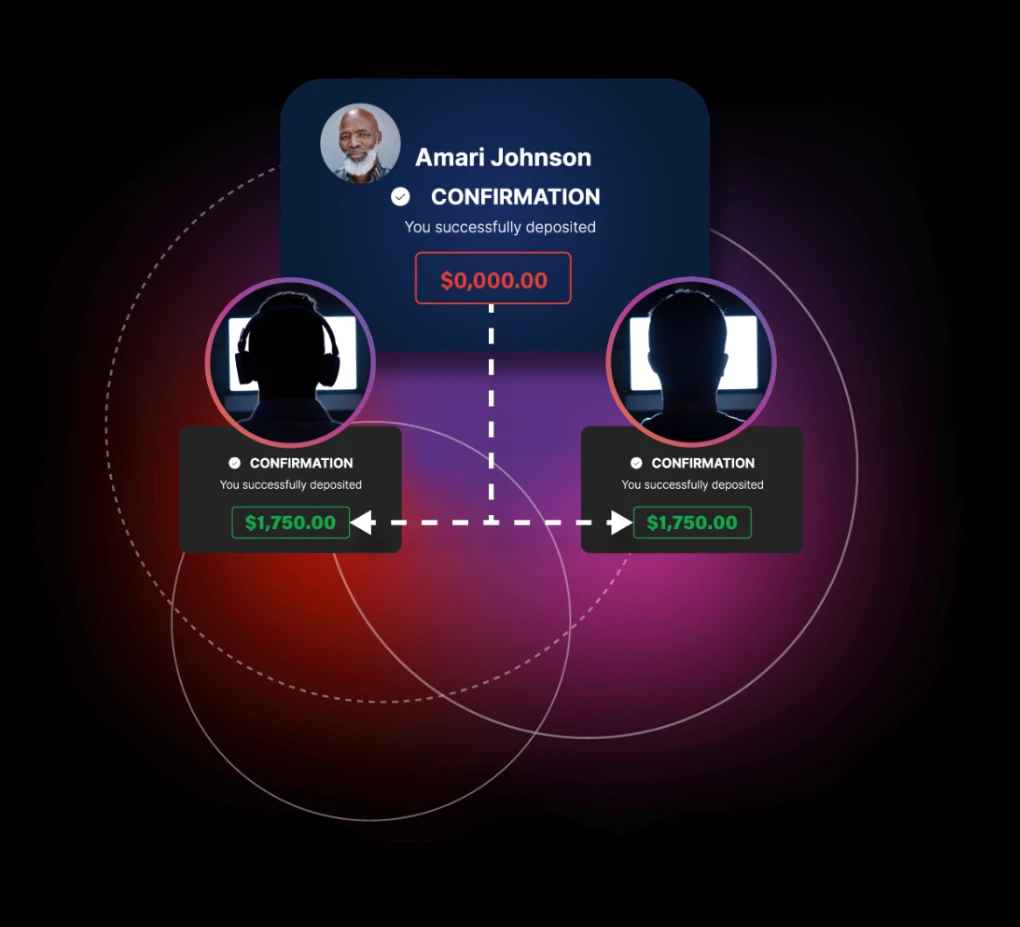
Crypto Cashout: When Fraudsters Join Forces
Click through the timeline to see how the scam works.