The Sift Fraud Intelligence Center
Stay ahead of emerging threats with industry data, consumer trends, and practical guidance for smarter fraud prevention.

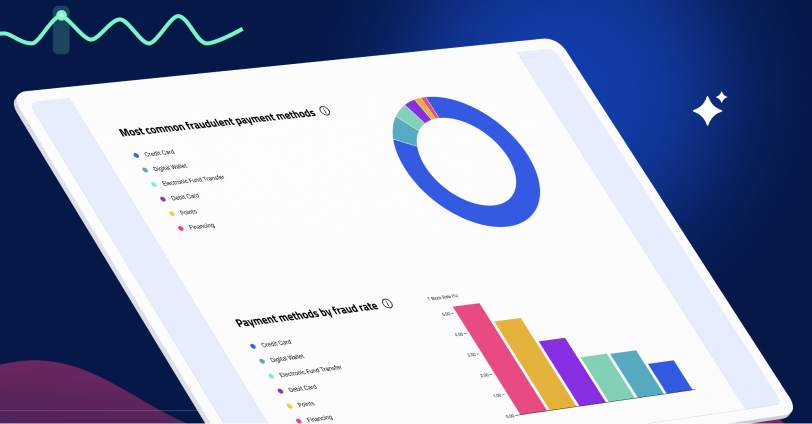
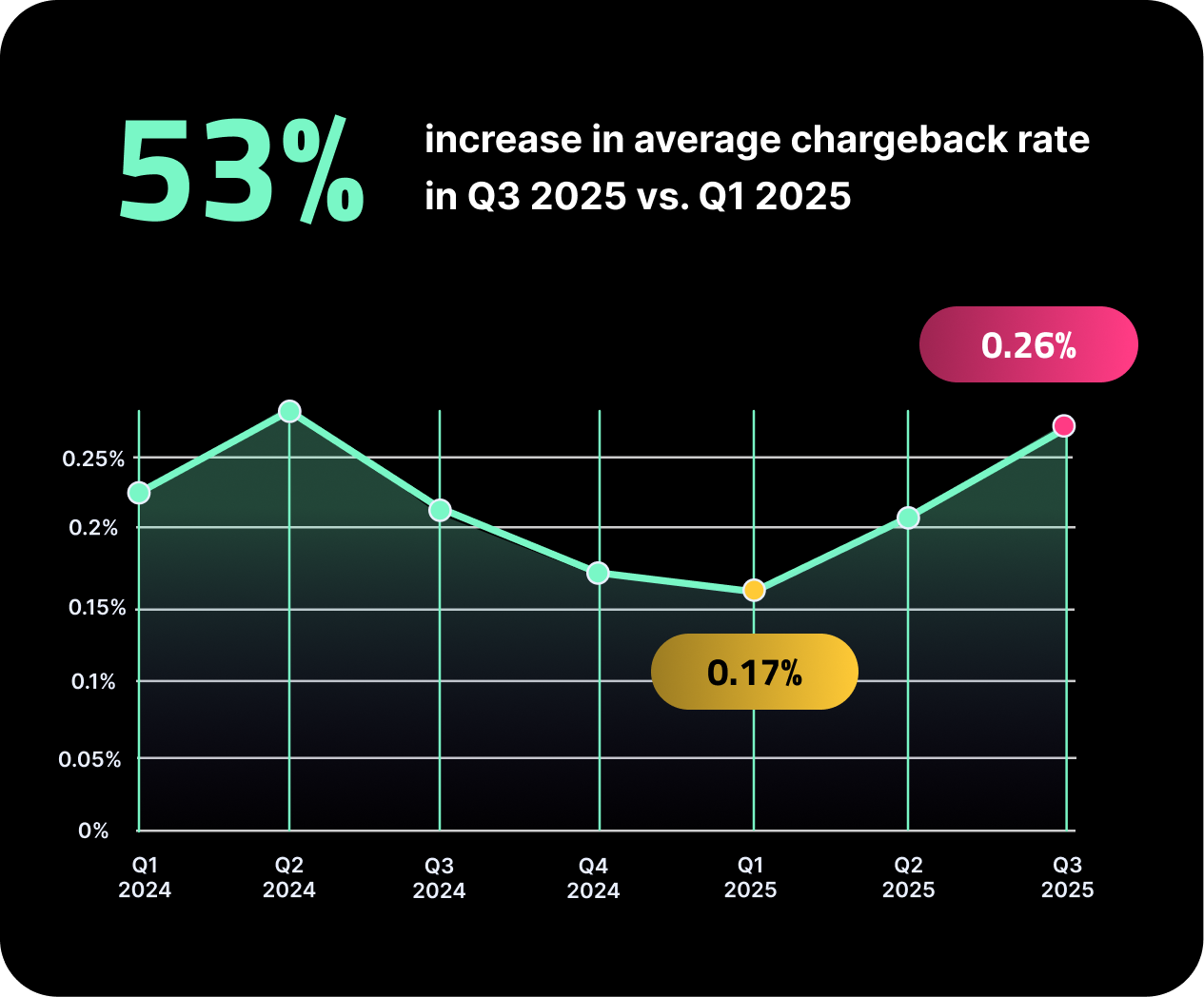
Current Fraud Trends

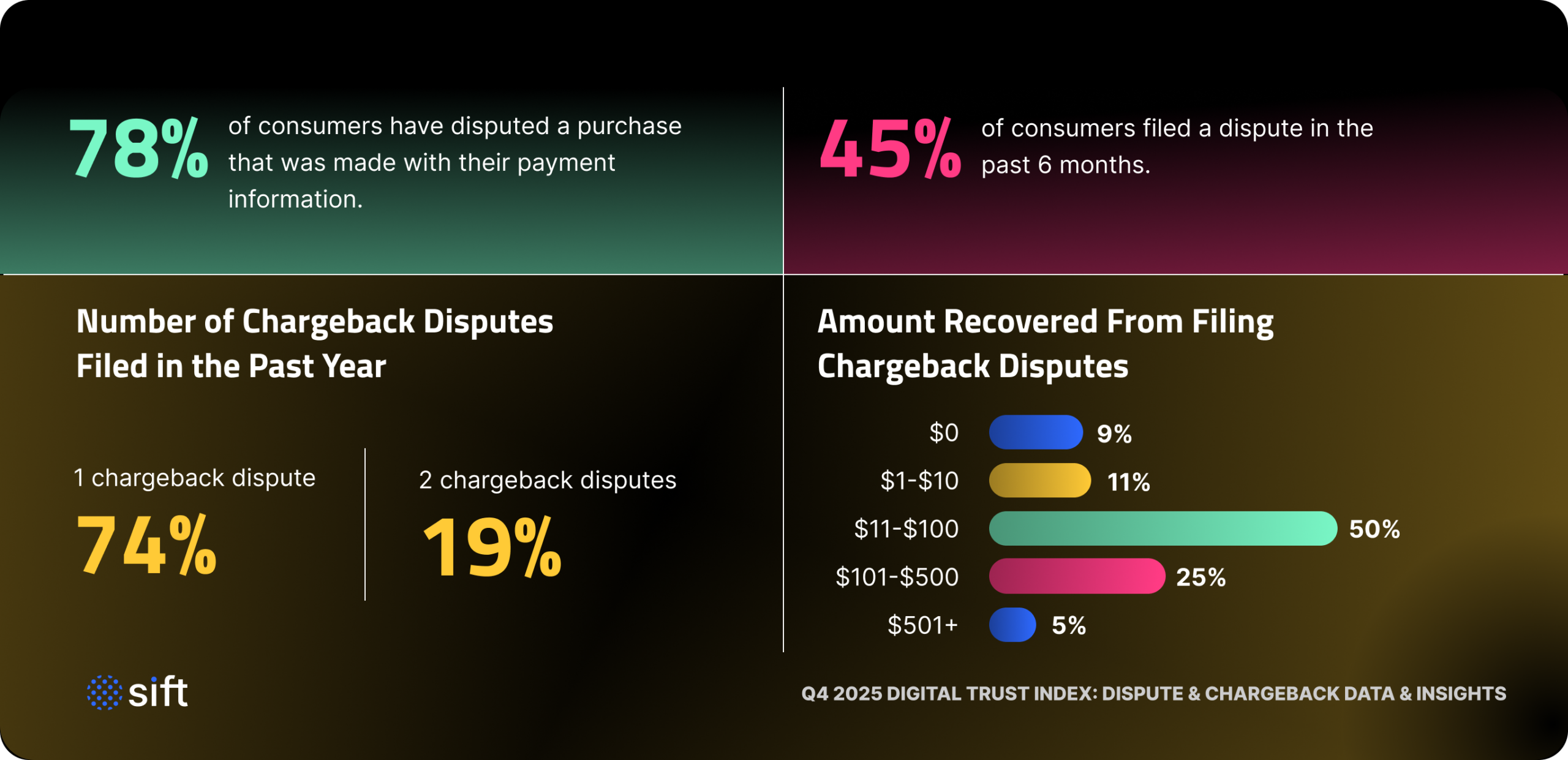
*On behalf of Sift, Researchscape International polled 1,075 adults (aged 18+) across the United States via online survey in October 2025.
Fraud's Impact on Customer Loyalty
Percent of consumers who would abandon a brand due to fraud
68% of consumers would no longer use or shop on a site where they had been a victim of payment fraud.
68% of consumers would no longer use or shop on a site where they had been a victim of payment fraud.
75% of consumers would stop using a site where they experienced ATO.
68% of consumers would stop using a website completely if they encountered fake or misleading content on it.
62% of consumers would shop less or not at all with a brand after a chargeback caused by fraudulent use of their payment information.
Data represents responses to multiple surveys of U.S. adults conducted by Sift between 2020–2025.
Expert Insights
Our Trust and Safety team uncovers the latest scams, discusses the future of fraud, and shares the biggest fraud threats facing digital businesses today.
As disputes and chargebacks continue to rise, and first-party fraud becomes an increasingly significant part of overall dispute volume, businesses face growing operational and financial pressures. Leveraging proactive fraud prevention and streamlined dispute management helps companies reduce losses, protect revenue, and maintain long-term customer trust.
Alexander Hall
Trust and Safety Architect at Sift
Tools & Resources
About This Center
The Sift Fraud Intelligence Center was built to centralize knowledge, tools, and alerts about digital fraud and abuse trends. Sift’s award-winning fraud prevention platform delivers digital trust at scale to leading global businesses across multiple industries. Our deep investments in machine learning, a data network scoring 1 trillion events per year, and a commitment to long-term customer success empower more than 700 customers to grow fearlessly.